23 January 1997
Macro viruses are the latest development in the battle against computer viruses. First encountered in the autumn of 1995 they have quickly caught the imagination of the press and virus-author alike. Their introduction into the virus world has caused a stir because they have broken some of the established "rules":
- They are the first ever viruses to infect documents rather than executable files. The first macro viruses seen infected Microsoft Word for Windows documents. In January 1996 the first AmiPro macro virus (APM Green Stripe) appeared. It should be remembered that other word processors could be at risk in the future. XM.Laroux, which appeared in July 1996, is the first working macro virus which infects Microsoft Excel for Windows spreadsheets.
- They are the first ever multi-platform viruses - not just capable of infecting PC systems, but Macintosh as well.
This document provides an overview to some of the better known macro viruses:
WM.Atom | WM.Concept | WM.Concept.B.Fr | WM.Divina | WM.DMV | WM.FormatC | WM.Friendly | APM.Green Stripe | WM.Hot | WM.Imposter | WM.MDMA | WM.NOP | WM.Nuclear | WM.Nuclear.B | WM.Polite | WM.Wazzu | WM.Wiederoffnen | WM.AntiDMV | WM.Colors | WM.Colors.B| WM.Nop | WM.Phantom | WM.Telefonica | WM.Xenixos | XM.Laroux| WM.Extra|
WM.ATOM
Description
ATOM consists of four macros: AutoOpen, FileOpen, FIleSaveAs, and ATOM;
all of these are execute-only.
When an infected document is opened, ATOM infects the global template (if the auto macros are disabled, the virus is rendered ineffective). ATOM does not turn off prompting when saving the global template; so if prompting is turned on, you will be prompted to save changes to the global template at the end of the Word for Windows session.
After the global template is infected, ATOM calls its first destructive payload. If the current date is 13 December, the virus deletes all files in the current directory.

Once the virus is active (that is, it has infected the global template), it infects all documents which are saved via the FileSaveAs command, or which are opened via the FileOpen command. If the seconds field of the current time is 13, at the time of infection , the virus encrypts the document being saved with the password "ATOM#1".
WM.Concept
Description:
This was the first virus to infect data files. Concept infects Microsoft
Word 6 documents (*.DOC) and the NORMAL.DOT template. The virus makes use
of the well-developed macro language, Word Basic, in an attempt to exploit
the fact that computer users exchange documents far more often than programs.
When an infected document is opened under Microsoft Word for the first time, the virus gets control as an AutoOpen macro; and infects the NORMAL.DOT template (or any other template, if it has been selected as a global default template). A message box, with the text '1', appears on the screen:
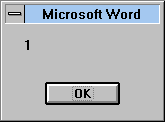
After this, every document saved using the File|SaveAs is infected with the virus. This normally happens when a newly-created document is saved to disk.
If Tools|Macros is selected and the macros are listed, the presence of the macros named AAAZFS, AAAZAO, AutoOpen, PayLoad and FileSaveAs indicates that the Microsoft Word system is infected with WM.Concept.
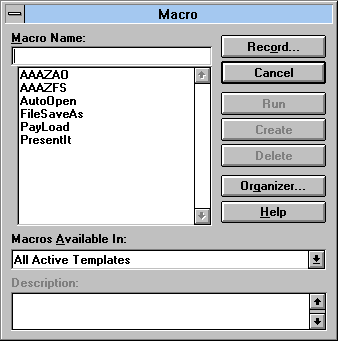
This virus works under versions of Microsoft Word for Windows 3.x, Windows 95, Windows NT and Macintosh. This made it the first ever multi-platform virus.
WM.Concept virus is a very common 'in the wild' virus. This is largely due to Microsoft accidentally shipping it on a CD ROM called Microsoft Windows 95 Software Compatability Test to hundreds of OEM companies, in August 1995. Another company distributed more WM.Concept-infected documents on 5,500 copies of a CD ROM called Snap-on Tools for Windows NT shortly afterwards.
WM.Nuclear
Description
A Microsoft Word for Windows DOC file, containing a description of WM.Concept,
was uploaded to one of the publicly accessible ftp directories at the US
internet provider netcom.com . The file turned out to be infected with
a new macro virus WM.Nuclear.
Similar to WM.Concept, the WM.Nuclear virus infects NORMAL.DOT when an infected document is opened. It then infects all the documents being saved using File/SaveAs. Unlike WM.Concept, all macros in Nuclear are "execute-only"; that is, they are protected (encrypted) in such a way you cannot view, or modify, their source code (the macros names can still be viewed using Tools/Macro). In spite of this, we were able to decrypt the macros, to analyse and understand the virus.
An infected document (or NORMAL.DOT) contains nine macros named AutoExec, AutoOpen, DropSuriv, FileExit, FilePrint, FilePrintDefault, FileSaveAs, InsertPayload and PayLoad. The main effect of the virus, besides replication, is that if a document is being printed, and the system clock seconds counter is in between 55 and 59 seconds (that is, with a probability of approximately 1/12th), two lines are added to the document and are subsequently printed at the end of the last page:
And finally I would like to say:
STOP ALL FRENCH NUCLEAR TESTING IN THE PACIFIC!
The virus was also supposed to drop a "normal" (that is, COM/EXE/NewEXE infecting) virus named PH33R (pronounced 'fear'), but due to a whole set of bugs it fails to achieve this.
Another of WM.Nuclear's payloads is designed to trigger on 5 April, in any year; this destructive macro, called Payload, was supposed to damage (truncate to 0 bytes) the system files IO.SYS, MSDOS.SYS and COMMAND.COM. Once again, however, this payload fails to work, due to bugs in the code.
The virus also causes some side effects such as error messages if you choose <Cancel> from File/Print or File/SaveAs.
Hot
Description:
WM.Hot creates an entry in the WINWORD6.INI configuration file, with a
'hot date', 14 days in the future, when its payload will trigger.
The virus activates randomly, within a few days of the 'hot date'; when the user tries to open a document, its contents are erased instead.
The payload is disabled if C:\DOS\EGA5.CPI is found to exist. A comment in the virus source code suggests that this is a 'feature' designed to protect the virus author and his friends.
WM.DMV
Description:
WM.DMV is the name of a Word for Windows macro virus written for "demonstration"
purposes by an American computer user. He subsequently made his virus available
for all to download via the World Wide Web.
The author of this virus also attempted to write an Excel macro virus; but this fails to work because of a bug.
WM.Divina
Description
Like WM.DMV, WM.Divina virus contains just an AutoClose macro; this macro
is an execute-only. When an infected document is loaded under Word for
Windows, and then closed, the virus infects NORMAL.DOT. Any document closed
after this will be infected.
The virus has two payloads:
(1) If a document is being closed during the 17th minute of any hour, a set of dialogue boxes are displayed, with pauses and beeps in between. The first says
"ROBERTA TI AMO!"
Then
"Virus 'ROBERTA' is running. Hard Disk damaged. Start
antivirus?".
Next comes
"Exit from system and low level format are recommended."
and finally
"Exit from System?".
After this the virus exits Windows. So, while the virus has no destructive payload as such, it might well succeed in persuading an average user to reformat his/her hard disk.
(2) Another payload triggers on 21st May, if a document is being closed between 10th and 20th, or between 40th and 50th minute of any hour. Two dialogue boxes are displayed:
"DIVINA IS THE BEST!"
followed by a box titled "Virus 'DIVINA' in esecuzione" and containing some message in Italian. After that the virus quits Windows.
Judging by the language, style, variables and subroutine names, it is certain that WM.Divina was written by the same person who wrote WM.AntiDMV. WM.AntiDMV is fairly widespread in Italy, Malta and Spain (but should have stopped replicating after June 1, 1996). Thus, AntiDMV could infact be 'WM.AntiDivina'.
WM.Xenixos
Description
This virus was distributed in a file named 'NEMESIS.ZIP' on an Internet
newsgroup, back in February 1996, and so has received broad initial distribution.
Its further spread has been somewhat limited by the fact that it is written to exploit only the German-language version of Microsoft Word for Windows. It will infect the global template file of an English Word for Windows user, but will NOT replicate further.
WM.XENIXOS watches for attempts to print files while it is active; and about half the times this happens it adds the phrase
"Brought to you by the Nemesis Corporation, © 1996"
to the end of the document printing.
When files are saved, the virus encrypts them with the file password "xenixos" just over half the time. WM.Xenixos replaces the Tools|Macros command with code that will display an error message instead of the activating Word for Windows' built-in macro viewer/editor, so it is not so easy to see that the virus macros are in place.
One other interesting effect is that WM.Xenixos tries to plant, and arrange to have activated, a variant of the DOS multipartite virus known as Neuroquila, when files are saved after March 1. It succeeds in planting this DOS virus, but not in running it. The Neuroquila variant planted has a bug, so it only infects boot sectors and not (in addition) programs.
AUTOEXEC.BAT is altered to call the Neuroquila virus.
WM.Imposter
Description
At the beginning of March, 1996, a new virus (very closely related to WM.Concept)
was discovered in England by Dr Solomon's Virus Lab. researchers.
It contains code similar to that found in both the WM.DMV and WM.Concept viruses. In fact, one of its macros is always named DMV. Like WM.Concept, it contains a Payload macro, but this one says
"just to prove another point".
It was named WM.Imposter due to its attempt to appear as either WM.DMV or WM.Concept and (hopefully) fool anti-virus products, an attempt at which it is generally unsuccessful.
WM.MDMA
Description
WM.MDMA is a macro virus, infecting Microsoft Word for Windows documents.
The virus is encrypted and uses just an AutoClose macro.
This virus, which has been reported 'in the wild', includes different payloads for DOS/Windows 3.x, Windows NT, Windows 95 and Macintosh. The payload triggers on the first day of any month.
The payloads for each operating system are as follows.
On machines running DOS/Windows 3.x, the virus overwrites AUTOEXEC.BAT with the following commands:
@echo off
deltree /y c:
@echo You have just been phucked over by a virus
which, after the first re-boot, will clear the entire hard disk (if DELTREE is found) and display the above message.
On machines running Windows NT, the virus deletes all files in the root directory.
On machines running Windows 95, the virus modifes system settings - 'Sticky Keys, High Contrast and Network Logon sequence. It also deletes the file C:\SHMK, *.HLP, in C:\WINDOWS\ and all *.CPL files in C:\WINDOWS\SYSTEM\.
On Macintosh machines, the virus attempts to delete all files on the disk.
After the payload has terminated, the virus displays a message box entitled MDMA_DMV, containing the following text:
You are infected with MDMA_DMV. Brought to you by MDMA (Many Delinquent Modern Anarchists).
WM.Wazzu
Description
WM.Wazzu contains only one macro, AutoOpen. Since the name of the AutoOpen
macro is the same in all language versions of Word for Windows, this is
the first virus that will replicate equally effectively in all international
versions of Word for Windows.
WM.Wazzu has an interesting payload. When the infected document is opened, the virus calls a routine three times; each time there is a 20% probability that the virus will move one word to a random place in the document. There is then a 25% probability that the virus will also insert the word 'wazzu' at a random point in the document. The virus then returns to the beginning of the document.
WM.Nuclear.B
Description
A variant of WM.Nuclear, altered from the original virus apparently by
some curious and inept, user messing around with it, was discovered in
a corporation in France in early March 1996.
Since the original WM.Nuclear virus was encrypted, it is likely that the user obtained the unencrypted source from where it was posted (on an Internet newsgroup created for the distribution of viruses and the promotion of virus writing) and worked from that to create this new variant.
WM.Nuclear.B does not try to plant the 'PH33R' virus, but calls other destructive routines from the original virus instead at that point.
This variant does not replicate in encrypted form, so it will be much easier for others to learn from, and it is to be expected that advanced macro virus programming techniques from this virus will start showing up much more often in future viruses.
WM.Polite
Description
In late March 1996, a new macro virus named WM.Polite was discovered in
the USA. It installs only FileClose and FileSaveAs replacement macros,
and so avoids detection by anything watching auto macros.
WM.Polite is rather odd, in that it prompts the user each time before it infects a document (it displays a dialog with the title 'Propogation of the virus', containing the text 'Shall I infect the file?'). Unfortunately, it does not ask when it originally infects the global template. It is not expected to survive and spread well 'in the wild'.
WM.Colors
Description
WM.Colors infects Word for Windows documents. When an infected document
is opened under Word for Windows, the virus infects the global template(usually
NORMAL.DOT). Subsequently, every document created using File|New, or saved
via File|Save or File|SaveAs, is infected by the virus. The virus contains
the following macros:
AutoOpen, AutoClose, AutoExec, FileNew, FileExit, FileSave, FileSaveAs, ToolsMacro.
If macros with such names existed prior to infection, they are overwritten by the virus.
Surprisingly enough, the AutoExec macro in the virus is an empty macro; it does nothing. The possible aim of this could be to overwrite an existing AutoExec macro, which could contain anti-virus routines (for example, supplied by Microsoft).
WM.Colors can propagate even with AutoMacros disabled (by invoking Word for Windows as WINWORD.EXE/mDisableAutoMacros, or by using one of Microsoft's recent anti-virus template tools). As soon as a user chooses File|New, File|Save, File|SaveAs, File|Exit or Tools|Macro, the virus gets control and infects NORMAL.DOT.
Unlike other known Word for Windows viruses (WM.Concept, WM.Nuclear, WM.DMV), WM.Colors virus cannot be spotted by using Tools|Macro to list active macros. The virus intercepts Tools|Macro and effectively disables it, while still using it for infection. For this reason, WM.Colors can be called the first macro virus with some stealth capabilities. Nevertheless, one can use File|Templates|Organizer|Macros to view the names of virus macros and even to delete them.
As in the case of WM.Nuclear (the first encrypted macro virus), all macros in WM.Colors are Execute-Only, and thus cannot be viewed/edited by means of Word for Windows.
The virus also enables AutoMacros and disables Word for Windows' prompt save changes to NORMAL.DOT.
The virus maintains a counter named 'countersu' in the (windows) section of WIN.INI file. Every time a virus macro is called (with the exeption of AutoExec), the counter is incremented by one. That is, every time a user opens, creates, saves, closes a document, attempts to use Tools|Macro or exits Word, the counter is incremented. When the counter reaches 299, and each 300th time thereafter (that is, 299, 599, 899, and so on), the virus triggers. It then changes Windows colors settings(text, background, buttons, borders, etc.) to randomly selected colors. So that the next time Windows is started the user is puzzled by the most unusual and weird color pallette.
WM.Telefonica
Description
Discovered in late April 1996, WM.Telefonica is another German-only Word
for Windows virus. It tries to create and execute an encrypted COM file,
via debug, in 1 out of 60 infections.
It replicates using MacroCopy to replicate its set of seven macros, including FileNew, FileOpen, FileClose, AutoOpen and Autoexec.
This virus was first reported attached to a document which was an order form, in German, for a set of erotic videos.
WM.Phantom
Description
WM.Phantom, another multi-language macro virus, was discovered in early
May 1996, in Germany.
The only macro attached, AutoOpen, is language independent. It is also encrypted. WM.Phantom can only replicate through this AutoOpen macro.
When decrypted, it appears to have been written by children in a high school. It displays some silly messages, including
"Hi sexy!"
and
"Guess who?".
WM.Friendly
Description
This virus (German in origin) was discovered in mid-May 1996. It shows
signs of having been written by the same person as WM.Telefonica. It creates
an INI file entry
[FRIENDS]
in which it sets:
Author=Nightmare Jocker
WM.Friendly attempts to be bi-lingual by containing a complete set of its macros in English, as well as a complete set in German! This brings the total macro count to 20 macros. Unfortunately for the author, who apparently did not have a copy of Word for Windows in English to test with, his English set of macros are improperly saved; as a result, the virus does not work under English versions of Word for Windows after all.
When WM.Friendly replicates under German Word for Windows, it plants a copy of a variant of the old DOS virus Little Brother.
WM.Concept.B.Fr
Description
In early March 1996, someone translated the FileSaveAs macro’s name, from
WM.Concept, into the French equivalent, producing a French-only version
of WM.Concept. This infected a large site within France. This is the only
difference between it and the original WM.Concept virus.
WM.FormatC
Description:
This is NOT a virus, but a macro trojan (it does not replicate). It does,
however, format the user's C drive as soon as the document is opened.
This trojan was posted to a Usenet newsgroup.
WM.Wiederoffnen
Type: Word macro trojan
Description:
WM.Wiederoffnen is NOT a virus, but a macro trojan. It comes in a Microsoft
Word for Windows 2 document, but also works perfectly under Word for Windows
6.
WM.Wiederoffnen intercepts the AutoClose macro and, when the document is closed plays tricks with AUTOEXEC.BAT.
APM.Green Stripe
Description:
This virus infects Ami Pro document files (*.SAM); for every SAM file a
corresponding SMM (Ami Pro macro) file with the same name, in the same
directory; it links SAM to SMM in such a way that opening SAM file invokes
execution of the SMM macro. The SMM macro files are hidden and cannot be
seen with a simple DIR command (although DIR/AH will work).
When an infected document is opened, the virus gets control and infects all *.SAM files in the current directory, which is always Ami Pro's default DOCS directory (...\AMIPRO\DOCS). The process is very noticeable since all the document files are opened and then closed, one by one; and a user is able to see them quickly appearing and disappearing on the screen.
Then the virus intercepts File/Save and File/SaveAs commands. On File/SaveAs, the virus infects the document being saved; and this is the only way the virus can propagate to another PC. Since both SAM and SMM files are necessary for the virus, and since a SAM file contains an absolute pathname as a reference to the appropriate SMM file, if the user simply copies either SAM, or both SAM and SMM files, to a floppy disk and then opens the SAM file under Ami Pro on a different PC, the virus will not run. However, when a document (SAM) is copied using File/SaveAs both SAM and SMM files are transferred and the pathname link is changed accordingly.
File/Save was supposed to be used for the virus' payload. On File/Save, the virus should replace all occurences of its in the document with it's. However, in our experiments, this did not appear to work.
Unlike other (Word for Windows) macro viruses, this Ami Pro macro virus is very unlikely to be transmitted via e-mail. This is due to the fact that Ami Pro keeps macros in separate SMM files, while only SAM files are sent as a e-Mail attachments.
The name of the virus, APM.Green Stripe, is taken from the virus itself. Its main macro procedure is called 'Green_Stripe_virus'.
Detection of APM.GreenStripe is made easier by a number of factors.
1) As mentioned above, when an infected document is opened, it is very noticeable; the screen keeps blinking as numerous documents are loaded and then closed.
2) After loading a document, the user can use Tools/Macros/Edit to see whether the document has an appropriate macro file (with the same name, but with the extension SMM) assigned to it, to be executed on open. The report will contain the names of all infected (and now deleted) SMM files. Then the user can run Ami Pro; and for each SMM file listed in the report, load the SAM file with the same name (there will be an error message reporting that the appropriate SMM file was not found), then use Tools/Macros/Edit and un-check the Assign box(es).
WM.NOP
Description
WM.NOP is a Word for Windows macro virus, reportedly ‘in the wild’ in Germany.
In order to spread, this virus requires the German version of Microsoft Word for Windows 6.0, or above; under other language versions of Word for Windows, the virus will infect NORMAL.DOT but will not spread further.
Documents infected with WM.NOP contain the macros AutoOpen and NOP. When an infected document is opened under Word for Windows, the virus gets control via the AutoOpen macro and infects the NORMAL.DOT global template. In an infected NORMAL.DOT, the AutoOpen macro becomes NOP; and the NOP macro becomes DateiSpeichern [German for FileSave].
WM.NOP has no payload.
WM.AntiDMV
Description
WM.AntiDMV is a Word for Windows macro virus, reportedly 'in the wild'
in Italy, Malta and Spain and probably some other Mediterranean countries.
This virus was designed to spread until 1 June 1996; and should, therefore, have stopped spreading at this time. However, it is possible that many infected documents and templates may exist ‘in the wild’.
WM.AntiDMV contains only one macro, AutoOpen. If an infected document is opened under Microsoft Word for Windows, the current year is before 1997 and the current month is before the 6 June, the virus infects NORMAL.DOT. The virus also removes the macro AutoClose from documents and templates, if it exists.
It is the time-limited feature, plus the removal of the AutoClose macro, which prompted the name of the virus; it effectively removes the DMV virus.
XM.Laroux
Description
XM.Laroux (a Microsoft for Excel macro virus) is the first macro virus
for Microsoft Excel which actually works.
So far (July 1996) there have been only two reported cases of the virus, on different continents (one in Africa, another in Alaska). This virus is not currently considered to be widespread.
The virus intercepts Excel's Auto_Open automacro. When an infected spreadsheet is opened, the virus activates and checks whether the system is already infected. If not, the virus creates an Excel file named PERSONAL.XLS in the Excel default startup directory, XLSTART (for example, C:\MSOFFICE\EXCEL\XLSTART) and copies itself there. The spreadsheets and macros from that directory are automatically loaded whenever Excel is run. From then on, every spreadsheet being opened, or created, on an infected system will become infected with the virus.
XM.Laroux does not have any intentional payload; it just replicates. The virus works under Excel for Windows, versions 5 and 7; running under Windows 3.x, Windows 95 and Windows NT. It does not work on Macintosh.
Infected spreadsheets contain a hidden sheet named 'laroux'.
Here is a fast check to tell whether you have the virus:
in Excel, go to Tools|Macro. If you see the macros 'auto_open' and 'check_files' and/or 'personal.xls!auto_open' and 'personal.xls!check_files', this indicates that your system is infected. Tools|Macro|Delete may be used to remove the virus macros.
WM.Extra
Description
WM.Extra (also known as 'Clock') carries its macros in encrypted form (execute-only).
The virus was written for the German version of Microsoft Word for Windows,
but it still replicates under other versions. It has been seen 'in the
wild' in Germany.
The virus has a non-destructive payload. If the following conditions are met:
year > 1996
minute > 39
day > 25
it displays a digital clock every two minutes.
WM.Colors.B
Description
In early April 1996, a prominent anti-virus researcher investigated what
appeared at first to be an outbreak of the ordinary WM.Colors macro virus
(see description for WM.Colors), in Portugal. When a sample of the virus
involved was examined, he discovered that it contained the WM.Colors virus,
except that the macro replacing AutoOpen was not from WM.Colors, it was
the one found in WM.Concept!
One likely explanation of how this 'hybrid' was formed is that a PC infected with WM.Colors was subsequently exposed to a document infected with WM.Concept. This replaced WM.Colors' AutoOpen macro with its own; and when the other code in WM.Colors caused WM.Colors to replicate, it copied the WM.Concept version of the AutoOpen macro to the target instead of its own AutoOpen, without checking. In any case, the virus still replicates, in its new form.